Release Notes / Customer Information
SR-Lenzspitze 06.07.2025
The Release Notes (RN) report on the enhancements, as well as new functionalities and changes to the eIAM Services as per the Roadmap FCh-DTI. Please direct your questions about the release to
Launch date
- REF: ⇨ 13.05.2025 ↴ ➽ SW updates & AGOV-First
⚒ Regression testing ❌❎ ✉➔ eIAM ⚒✅ - ABN: ⇨ 11.06.2025 ↴ ➽ SW updates only
⚒ Regression testing ❌❎ ✉➔ eIAM ⚒✅ - PROD: ⇨ 06.07.2025 ➽ SW updates only
Sunday ⚒ Final Inspection ❎❎ ✉➔ eIAM
- New SW versions for the eIAM components (REF to PROD)
- AGOV-First (REF environment only)
Regression testing by eIAM customers
Your cooperation is necessary and very important. In the last releases, we had problems in the higher operating environments (ABN, PROD) only where applications had not carried out their regression tests in advance on REF and/or ABN. These are unnecessary problems which we can avoid together. We count on your support here. It is important that you carry out your regression tests carefully and report any problems to the testing team promptly and in a qualified manner.Process and expectations for SR introductions
In order to be able to guarantee the stable and secure productive eIAM service, we require meaningful regression tests of the applications in the REF and ABN instances until the SR rollout to PRODUCTION. Normally you have 10 working days at your disposal for this. Please note that in the first 2 days after installation you can benefit from an Early Live Support Team that will assist you promptly in the case of problems.These release notes will help you to plan the regression tests in relation to the eIAM functionalities you use and will also serve as a source of information for your end customer communication. Please note that the final version of the release notes with all necessary details will be delivered shortly before the productive installation.
Important
Let us know your release test results (positive or negative) via Feedback form customer regression tests
eIAM contact person
If you have any questions or concerns about eIAM, ePortal or PAMS you can contact the following offices or persons;eIAM contact points
- Testing questions
- eIAM-Testing-Team: Testing-eiam@bit.admin.c
- Operational issues
- eIAM Platform Team:
eIAM-Operations@bit.admin.ch / +41 (0)58 469 88 55
Edgar Kälin FOITT (PO eIAM Platform Team) - Integration of new solutions
- eIAM Integration Team:
eIAM-Integrations@bit.admin.ch / +41 (0)58 469 88 55
Danny Rothe FOITT (PO eIAM Integration) - ePortal issues
- eIAM-ePortal-Team:
eportal@bit.admin.ch
Dilek Hoza FOITT (PO ePortal) - General questions, mgmt questions or complaints
- Roger.Zuercher@bit.admin.c
h , Service Manager eIAM / Project Manager (BO-eIAM) - New requirements for eIAM
- Show e-mail addres
s , service responsible for federated IAM (BO-eIAM)
Kadir Gelme (SM eIAM Testing)
Changes - Innovations
New SW versions for the eIAM components (REF to PROD)
As part of life cycle management, the eIAM components (reverse proxy policy enforcement points RP-PEP, identity providers CH-LOGIN, FED-LOGIN, IdP-Base and central IDM system) are updated to the latest software versions.AGOV-First (REF environment only)
Testing by the office
As you can see from the Release Notes, many changes will be implemented in eIAM with the introduction of AGOV-First.In principle, these changes are transparent for your specialised applications.
This means that the content of the token that your application receives from eIAM remains the same.
However, we would like to point out that the upgrade from CH-LOGIN to AGOV by users and the activation of the automatic updating of identity data (just-in-time provisioning) may lead to an increase in changes of e-mail address for users.
If a specialist application uses the e-mail address as a user identifier contrary to the recommendations of eIAM, this can lead to users no longer being recognised by the application due to the changed e-mail address.
If you have tested AGOV-First in the REFERENCE environment, please let us know about your experiences using Feedback form AGOV-Firs
Please note that the changes within the scope of "AGOV-First" will only be rolled out in the REF environment of eIAM with the release "Lenzspitze" and not in the ABN and PROD environment. In the ABN and PROD environment of eIAM, the rollout of "AGOV-First" will only take place with the next release "Liskamm". This procedure was chosen after consultation with our customers in order to give you, as eIAM customers, sufficient time to familiarise yourself with the changes within the framework of AGOV-First, to test AGOV-First extensively with your specialist applications and to give us feedback at an early stage. Before these changes become effective in production with the "Liskamm" release in September 2025.
AGOV is Swiss public authorities' login service. It can be used by federal, cantonal and municipal authorities.Thanks to new technology, you no longer need a user name and password with AGOV. This is safer and more convenient for users than using a password. AGOV is a Federal Service and has been available in the first government applications since the start of 2024. AGOV can also be used in eIAM since the beginning of 2024. However, still with restrictions as a "Bring Your Own ID (BYOI)" add-on to a CH-LOGIN account.
The project to replace CH-LOGIN with AGOV (CH2A) addresses the next step with the "AGOV-First" phase to make AGOV the authority login of choice in the Federal Administration as well. In the "AGOV-First" phase, the use of existing CH-LOGIN identities is still possible. The registration of new CH-LOGIN identities is also supported. The only exception is new, verified identities (with increased Quality of Authentication Level - QoA). Verified eGOV identities will only be offered via AGOV. This allows users to benefit from the fact that their fee-based verified identity can be used at all administrative levels.
AGOV as Switzerland's authority login is to be promoted as part of the "AGOV-First" phase. Users should be informed about AGOV and motivated to use AGOV. However, without exerting pressure on users. The secure switch from CH-LOGIN to AGOV should be made as easy as possible for users with an existing CH-LOGIN.
Up-to-date information about AGOV, CH2A and the current AGOV-First phase with the presentation and the use case demonstrations from the customer event on 11 April 2025 can be found on the eIAM Soundingboard
Standardisation of the selection of the login method (Home Realm Discovery)
As part of AGOV-First, the selection of the login method, i.e. the selection of the identity provider (HRD), has been revised and standardised. Previously, two different options were offered in eIAM. On the one hand, the so-called "tile view", which displayed all identity providers in the form of tiles. On the other hand, the so-called "CH-LOGIN First" view, which made it possible to log in directly to CH-LOGIN and use other identity providers as alternatives. In addition, the selection of the login method on small screens (smartphone) differed greatly from that on large screens (laptop/desktop). The different behaviour of eIAM has repeatedly led to confusion among users in the past. In addition, the behaviour is not compatible with the "AGOV-First" approach, in which AGOV is to be brought to the fore as the Swiss authority login for eGOV users. This is also the reason why AGOV is always offered as the primary identity provider in the new Home Realm Discovery for applications that support the eGOV context. An information box informs the user about AGOV as the Swiss authority login and motivates them to use AGOV.-
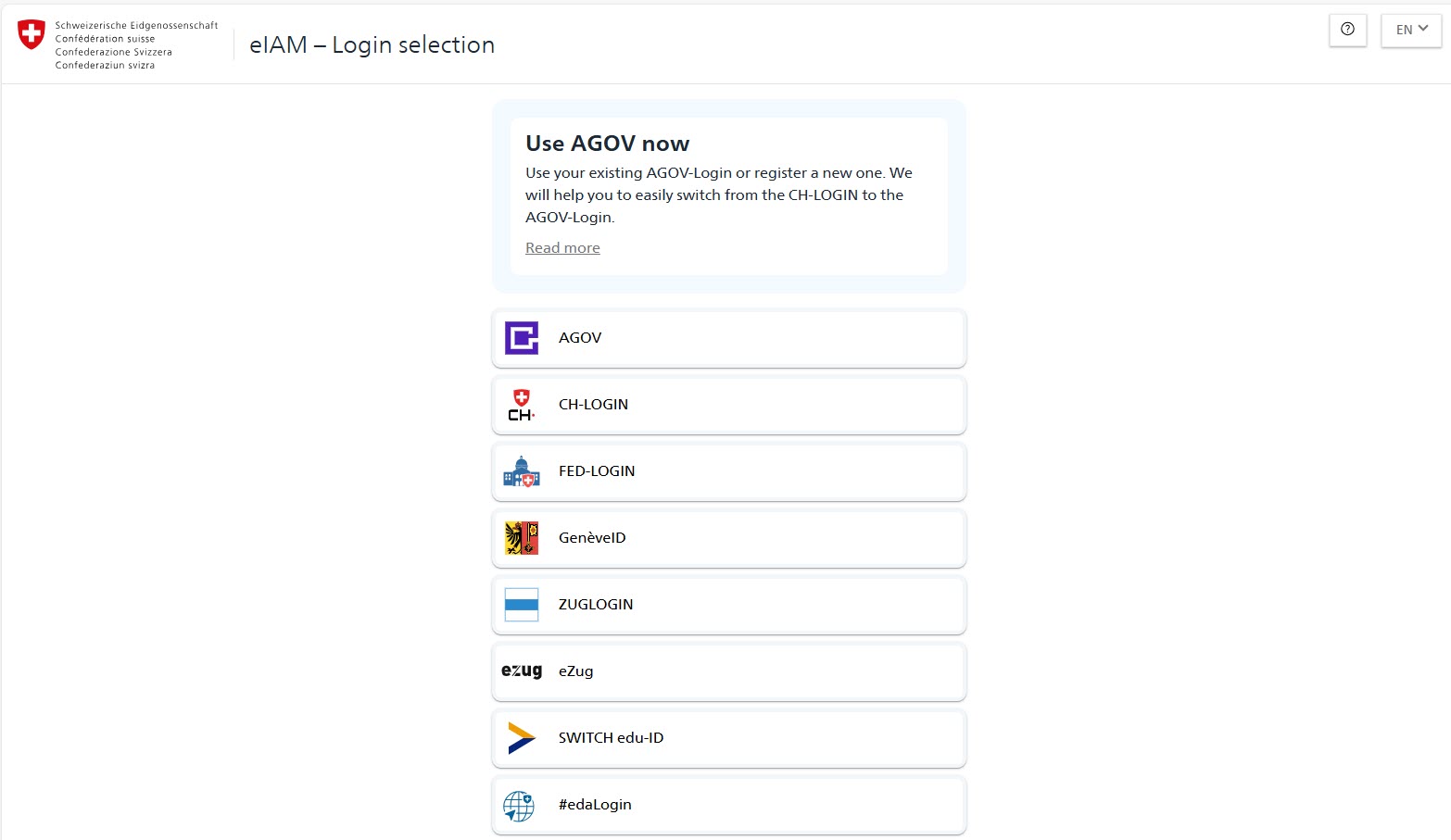
- Selecting the login method
-
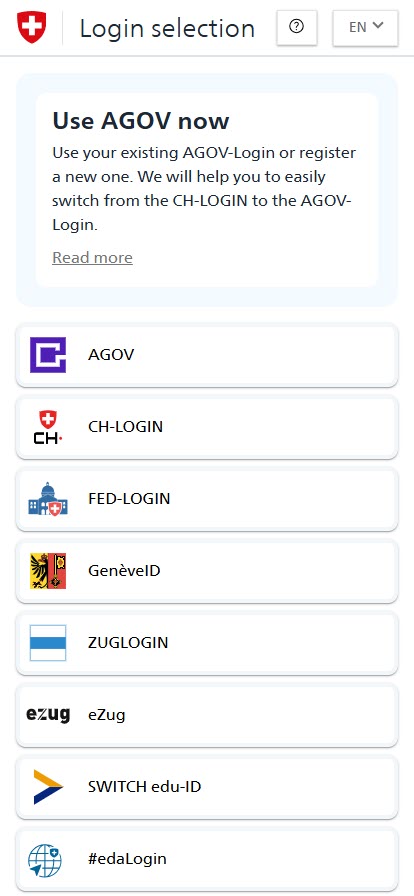
- Mobile view
Transparent blocking of unsupported login methods
eIAM supports different login methods and identity providers. These identity providers provide identities of varying quality. Generally up to a level of QoA30. This is sufficient for many Federal Administration applications in the eGOV context. If an application requires a higher quality of authentication, AGOV-First does not simply hide identity providers whose identities do not fulfil the requirement, but continues to display them to the user. However, they are marked as blocked for the user. The user is informed transparently as to why the identity previously used in eIAM cannot be used and how they must proceed in order to use the application they want to access in future. This improves the user experience in eIAM for applications with increased QoA requirements.Information about the eIAM QoA levels can be found here:
-
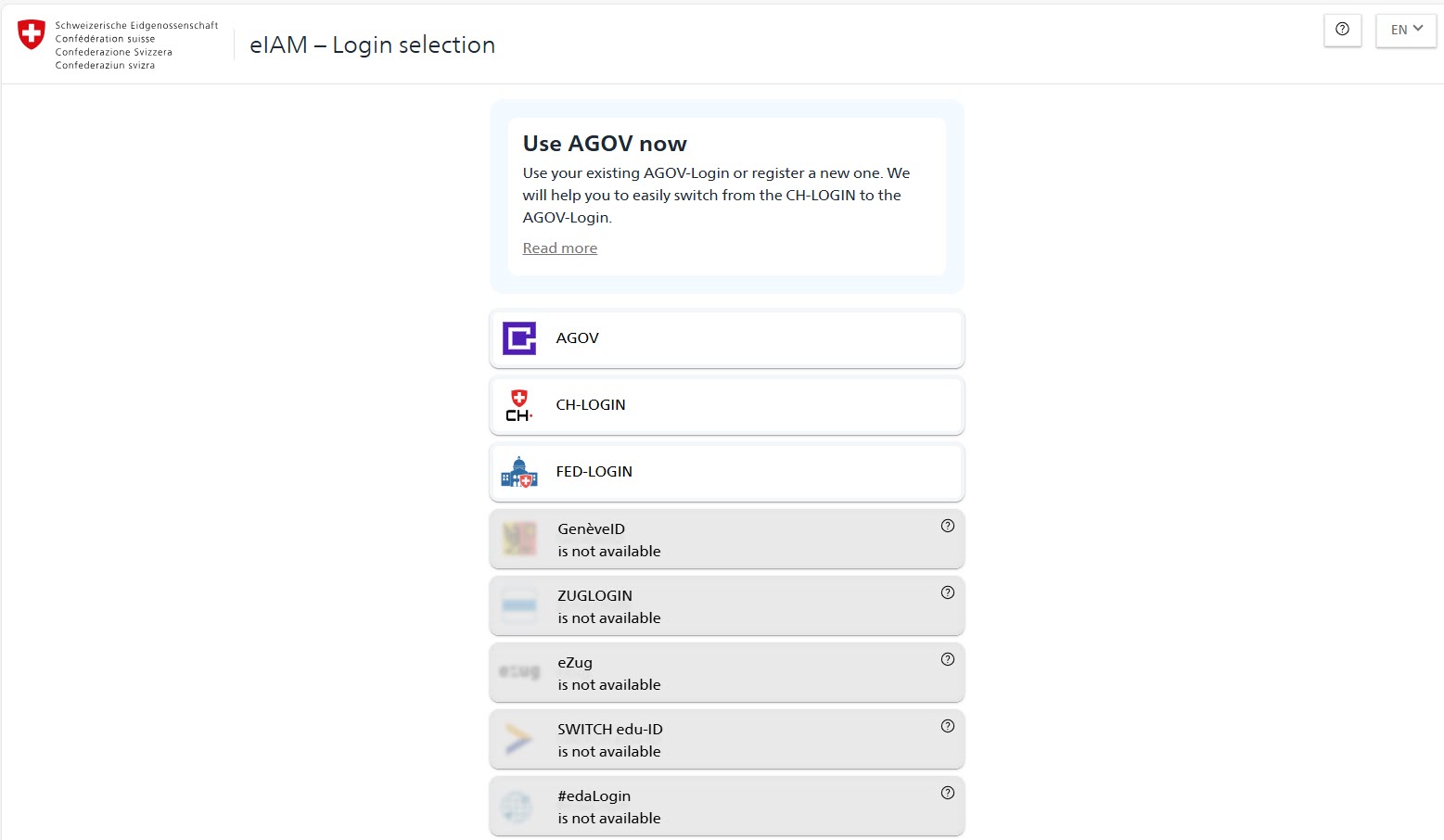
- Blocking of unsupported login methods
FED-LOGIN - Default login method in the networks of the Federal Administration
Most Federal Administration applications that are accessed by users from the Federal Administration networks expect the user to log in using the FED-LOGIN login method. There are a few exceptional cases in which a small group of users (e.g. testers) also want to use Federal Administration web applications from the Federal Administration networks with other identities (e.g. CH-LOGIN or AGOV). Previously, this meant that all users from the Federal Administration networks first had to select the login method (in most cases FED-LOGIN). AGOV-First corrects this behaviour in order to improve the overall user experience when authenticating applications from the Federal Administration networks. If FED-LOGIN is configured as one of the possible login methods for an application, FED-LOGIN is always automatically selected as the login method.Users with special requirements who want to override this behaviour can use the eIAM feature "Autologon Cookie" to override the automatic login with FED-LOGIN in the Federal networks.
Information on the use of the "Autologon Cookie" can be found in the eIAM Help: Testing without autologo
Support for users when upgrading from CH-LOGIN to AGOV-Login (Upgrade Wizard)
A wizard has been developed in eIAM to make it as easy as possible for the approximately 2.8 million users with an existing CH-LOGIN to switch securely from CH-LOGIN to AGOV-Login. When a user accesses eIAM for the first time with their AGOV login, the wizard determines whether there is a CH-LOGIN in eIAM that is registered with the same e-mail address as the AGOV login. If a corresponding account is found, the user is informed that there is a corresponding CH-LOGIN with the same e-mail address and he has the option of replacing the CH-LOGIN with his AGOV login. To do this, the user must prove that they are the rightful owner of the CH-LOGIN by logging in with their credentials registered in eIAM (password, if registered second factor). If no CH-LOGIN with the e-mail address reported by AGOV is found when logging in with AGOV-Login in eIAM, the user is asked whether they have a CH-LOGIN registered with a different e-mail address and whether they wish to replace it with their AGOV-Login or whether they do not have a CH-LOGIN at all. If the user wishes to use an existing CH-LOGIN, they must use the e-mail address of their CH-LOGIN, password and, if necessary, the second factor to authenticate themselves as the legitimate owner of the CH-LOGIN.In both cases, the eIAM identity is linked to the user's AGOV login and their previously used CH-LOGIN is archived. The user is informed that their CH-LOGIN has been deleted and that they must always use AGOV to log in in future. All access authorisations are retained during this process.
If the user confirms that they do not have a CH-LOGIN, a new eIAM identity is created for them.
Support for users when upgrading from CH-LOGIN to AGOV and recoveries
Of course, when users switch from CH-LOGIN to AGOV, we also expect situations in which the user can no longer use their CH-LOGIN login factors (password / second factor). In these cases, too, security must of course be the top priority. The recovery function for password and second factors is offered to the user by the wizard. However, in an optimised form that is as user-friendly as possible. For example, it makes no sense to have the user enter a new password or a new second factor in the recovery only for the change from CH-LOGIN to AGOV if the password and second factor are never needed again afterwards. In the recovery cases, the fallbacks to the defined replacement factors (e-mail account / security questions) are used to authenticate the rightful owner of the CH-LOGIN. However, unnecessary recording of login factors that are no longer required is consistently avoided.Support for users with verified CH-LOGIN identities when upgrading to AGOV
Users with CH-LOGIN identities that have been verified either via the so-called nHEC+ verification process (with video identification) or via the VASCO token issuance process retain their verification status and thus the QoA of their identity in eIAM even when upgrading their CH-LOGIN to AGOV-Login until the validity of the identity verification expires (5 years after performing the video identification or delivery of the VASCO token). This also applies if they carry out the upgrade with an unverified AGOV login. From the point at which the user uses their eIAM identity with a verified AGOV login, AGOV specifies the identity verification status.CH-LOGIN - Support for users after upgrading from CH-LOGIN to AGOV-Login
It is to be expected that users will simply forget that they have already made the switch from CH-LOGIN to AGOV in the past and later try in vain to log in with their former CH-LOGIN. The user will be informed by eIAM in the following cases that he has already upgraded to AGOV-Login:- User tries to log in with his former CH-LOGIN (identified via the e-mail address).
- User tries to recover the password of his former CH-LOGIN because the login does not work.
- User tries to register a new CH-LOGIN with the same e-mail address as his old CH-LOGIN or his AGOV-Login already used in eIAM.
CH-LOGIN - Support for new users when choosing an identity provider
With AGOV-First, after selecting CH-LOGIN and choosing to register a new CH-LOGIN, the user is informed about AGOV and motivated to register an AGOV login instead of a CH-LOGIN. However, the user is offered both options. They can choose whether they want to register an AGOV login or a CH-LOGIN. An exception to this behaviour is if the user has called up an application that requires a higher quality of authentication (> QoA30). In this case, the user is informed that new, verified identities are only offered with an AGOV login. In this case, the user only has the choice of registering an AGOV login or cancelling the registration.-
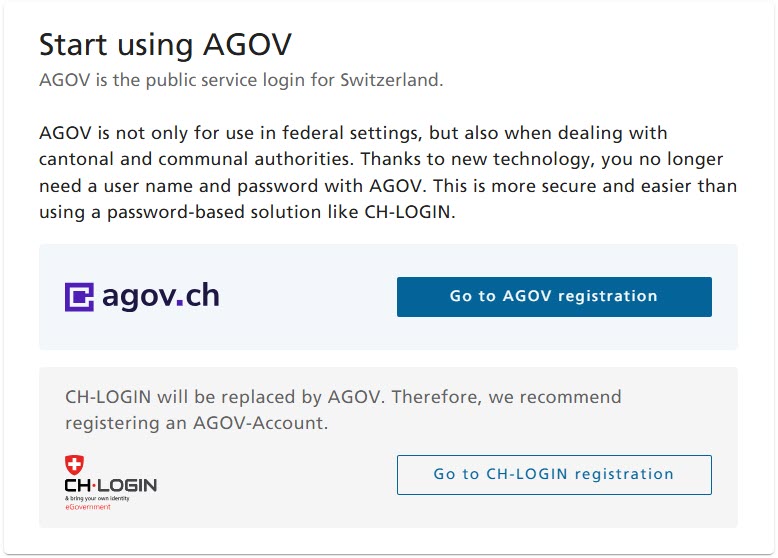
- Information about registering for an AGOV-Login instead of a CH-LOGIN.
CH-LOGIN - Fade-Out support VASCO token
Previously, it was possible with CH-LOGIN to register VASCO tokens issued by the BIT as a strong second factor. With AGOV-First, it is no longer possible to register VASCO tokens as a means of authentication for CH-LOGIN identities. CH-LOGIN with already registered VASCO tokens will continue to work with VASCO tokens as a second factor.Note: Please note that this explicitly refers to the re-registration of VASCO tokens for CH-LOGIN identities. The "OTP login" is a different login method. It is not affected by this change and should not be confused with the CH-LOGIN.

- CH-LOGIN TILE

- OTP-Login
CH-LOGIN - Fade-out of identity verification support with video identification
Previously, it was possible to upgrade CH-LOGIN identities with identity verification means at level "high" (Mobile ID / FIDO2 security key) from level QoA30 to level QoA50 by means of a verification process with video identification (VIPS). With AGOV-First, this upgrade is no longer offered for CH-LOGIN identities. Users who now require a verified identity in the eGOV context create an AGOV login, carry out the identification process in AGOV and upgrade their existing CH-LOGIN with their verified AGOV login.CH-LOGIN who had already completed this verification process before AGOV-First will retain their clarification status until the identification expires (5 years after the video identification was carried out).
AGOV - Support of verified AGOV identities in eIAM (QoA50)
Until now, AGOV identities could already be used in eIAM. However, AGOV identities were accepted in the same way as other so-called Bring Your Own Identity (BYOI) identities as an alternative login method in the CH-LOGIN context and only with a classification of "normal", i.e. the "medium" level according to Si001. Even if the authentication of the user has been carried out with a credential at level "high" and the identity of the owner of the AGOV login has been established by means of a high-quality clarification process. With AGOV-First, users can also use Federal Administration applications in the eGOV context with their AGOV login if the application requires a quality of authentication of "high" (up to QoA50).If the QoA level is too low, the user is notified after authentication that they require a verified AGOV-Login and is guided through the process of obtaining a verified AGOV-Login at QoA50 level. The procedure is described here: AGOV for the Federal Administration. Verified AGOV-Logi
With the release of Lenzspitze and the rollout of AGOV-First, AGOV identities can be used in eIAM up to a QoA level of QoA51. See also ‘AGOV – Support for AGOV identities with verified AHV numbers in eIAM (QoA51)’.
Information about the eIAM QoA levels can be found here:
AGOV - Support of AGOV identities with verified AHV number in eIAM (QoA51)
AGOV is able to provide the verified AHV number for persons with an AGOV login. The basis for this is a verified AGOV identity. By verifying the AHV number against the ZAS Register, AGOV verifies whether the AHV number actually belongs to this person. eIAM-integrated applications can now request the authentication quality QoA51. It should be noted that the application can then only be used with AGOV as the identity provider, as only AGOV can provide the verified AHV number. Of course, the application can then only be used by people who have an AHV number.If the QoA level is too low, the user will be notified after authentication that they require a verified AGOV-Login and will be guided through the process of obtaining a verified AGOV-Login at QoA51 level. The procedure is described here AGOV for the Federal Administration. Verified AGOV-Logi
Information about the eIAM QoA levels can be found here: